Information Security Management
Information Security Management
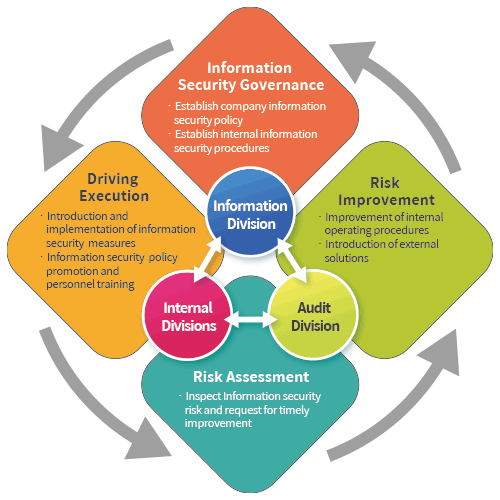
In order to reduce information security risks in the control and information security environment, FUBURG has been planning and supervising the implementation of information security system, organizational duties, document control, asset management, system development and maintenance, ERP system operation management, and internal control regulation compliance at the management level. And FUBURG established “Information Security Management Regulations”, covering computer systems, information security, network management, software and hardware maintenance, backup systems, personnel education, etc. The information technology division of our company is responsible for planning and formulating relevant policies and implementing corporate information security management measures, adjusting them to suit the local conditions of overseas locations, ensuring the normal operation of information systems and data preservation, and reducing information security risks.
FUBURG’s audit division is the supervisory department for information security monitoring and responsible for supervising the implementation of internal information security. If deficiencies are found, the audit division will be asked to propose specific improvement measures and the effectiveness of the improvements will be tracked regularly to reduce internal information security risks. The latest report date is November 12, 2024.
Information security policies and specific management programs
The information security management mechanism of our company contains the following four aspects:
- Nomothetic dimension: To establish the company’s information security management system and regulate employees’ operation behavior.
- Utilization of technology: Build information security management equipment and implement information security management measures.
- Employee education: Conduct information security education and training to raise the awareness of information security of all employees in the company.
- Back-up system: Conduct data back-up measures and regular disaster recovery drills.
The management measures are described as follows:
- Nomothetic dimension: FUBURG has established a number of internal information security regulations and systems to regulate the information security behavior of our personnel. And we regularly review annually whether the relevant systems are in line with the changes in the operating environment and adjust them in a timely manner according to the needs. Furthermore, we implement internal audits regularly to strengthen the management of our information security practices.
- Utilization of technology: In order to prevent various external information security threats, FUBURG not only adopts a multi-layer network architecture design, but also builds various information security protection systems to enhance the security of the overall information environment.
- Employee education: FUBURG educate our employees on the emergency notification and response methods in case of information security incidents regularly through education training or emails.
- Back-up system: In the face of increasingly powerful hackers and virus attacks, in order to protect the company’s important data, local backup mechanism and cloud backup mechanism have been established for the company and each business location to ensure the integrity of the data.
The information security management measures implemented by our company include the following:
Information security management measures
| Type | Description | Related Operations |
| Authority Management | Management measures for user accounts, privileges and system operation behavior |
|
| Access Managemen | Controls for personnel access to internal and external systems and data transmission pipelines |
|
| External Threats | Internal system potential weaknesses, poisoning pipes and protective measures |
|
| System Availability | System availability and disposal measures in case of service interruption |
|
In November 2023, our company established an information security director and information security personnel to coordinate and manage all information security operations. We regularly conduct vulnerability scans, checks on the effectiveness of protection systems, and other related security tests. We provide information security awareness and training courses, conducting 12 sessions of information security awareness for all employees in 2024. Although we have not purchased cyber insurance yet, we ensure a secure information environment through the operation of the company’s information department and the implementation and audit of information security policies. We aim to enhance the information security systems at all overseas locations to strengthen the company’s security network. Future plans include expanding our information security team and further training and certification to enhance the company’s information security capabilities, making it more reliable.
